
Why Pixl eKYC verification
software different?

In response to evolving regulatory mandates, an increasing number of Banks, NBFCs, and online businesses in New Zealand are now integrating eKYC Software into their identity verification processes. This shift is driven by the need for heightened security and compliance. Beyond enhanced security, video KYC also offers the advantage of speed and simplicity, making it the preferred choice for identity verification in the digital age.
With our advanced eKYC solution, New Zealand organizations can enjoy a more
robust and secure method of identity
verification.
Online eKYC & AML Solution for
Streamlined Customer Onboarding

AI-Based KYC Solutions for Everyone
Our cutting-edge facial recognition algorithms have undergone extensive training, encompassing a diverse range of facial characteristics, including variations across races, ages, and genders. This comprehensive training empowers our model to accurately identify individuals, irrespective of their racial background, age, or gender.
Our customer relationship management solution seamlessly integrates with leading eKYC service providers, ensuring a cohesive client acquisition journey. From application submission and verification to onboarding and closure, our integrated approach streamlines the entire eKYC process.
Seamless Integration for Effortless eKYC

OVD Checks
The Pixl eKYC solution cuts down on the necessity for bank employees to manually verify documents and have face-to-face meetings with customers. This leads to time and cost savings for banks, allowing them to offer customers reduced fees or improved products and services.
Spoofing is a big problem in the digital world. It's when fake videos try to look real. Our AI system fights against this by using strong anti-spoofing measures. These measures protect the eKYC process.
Robust Anti-Spoofing Measures

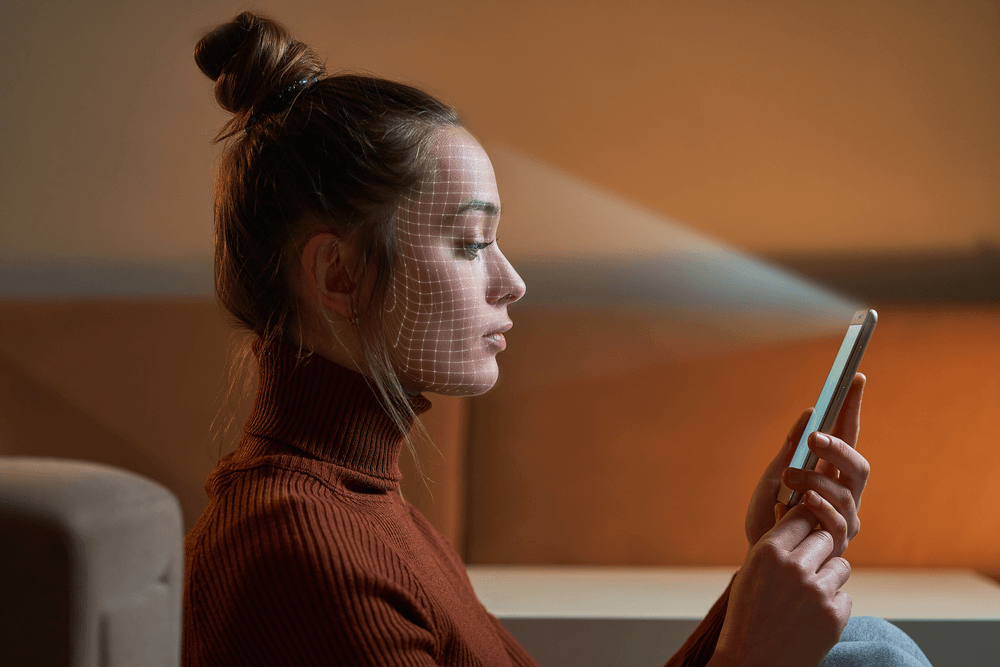
Liveness Detection for Enhanced Security
Within our face recognition solution, artificial intelligence and deep learning techniques are harnessed to verify real-time facial features against those on official ID documents. This rigorous validation process effectively detects fake photographs, providing an added layer of security against fraudulent activities.
For organizations seeking complete control over their data, hardware, and software, our on-premises solution offers a compelling option. With all operations confined to your facility's infrastructure, this approach minimizes third-party involvement, mitigating potential security and compliance risks associated with cloud-based alternatives.
On-Premises Control


Benefits of eKYC Solution in the Digitized World
New Account Opening
Instant Verification
Complete Automation
Trusted by Many
Enhanced Security
High-Assurance Transactions
Remote and Secure Customer Onboarding
Regulatory Compliance
KYC Process Scheduling

Comprehensive Interaction Platform
By incorporating Pixl eKYC software providers, you can enhance your customer's experience right away. Our software assists in tackling typical problems your customers could encounter. Through personalizing the experience, you can effectively clear up any confusion they may have and enhance their overall experience.
Ensuring Credibility with Digital eKYC Checks
Our commitment to authenticity extends to the meticulous detection and analysis of any alterations or manipulations within video footage. This forensic scrutiny not only ensures the credibility of video recordings but also serves as a valuable tool for risk assessment and spoof detection. By identifying any inconsistencies or modifications in a video,our investigative capabilities determine its integrity and credibility.
Customizable Dashboard
Our team is creating AI models that can operate in real-time, even in places with limited internet speed and on less powerful devices. This will allow us to adapt swiftly to new challenges and deploy our technology on a wide range of devices.
APIs Served for Industry
Our API is designed to assist various industries and seamlessly connects with customer management software to lower risks and boost efficiency. This greatly simplifies the process of automating data and information gathering.
FAQS
Frequently Asked Questions
Our Visitor management system is designed to adhere to data protection regulations. It employs encryption, secure storage, and regular audits to guarantee the confidentiality and integrity of visitor information.
In emergencies, the system provides instant access to a list of on-site visitors, aiding in quick and efficient evacuation procedures and ensuring everyone's safety.
TheVisitor management system allows for quick registration of unexpected guests or VIPs, offering priority check-in and immediate notifications to the designated hosts for a personalized welcome.
Our Visitor management system employs advanced security protocols, including multi-factor authentication and encrypted data transmission, to safeguard visitor data from unauthorized access or breaches.
Yes, our visitor management system includes analytics features that offer valuable insights into visitor demographics, patterns, and behavior, assisting in optimizing facility management and enhancing the overall visitor experience
The system promotes sustainability by minimizing paper usage through digital check-ins and reducing energy consumption with efficient hardware. It aligns with eco-friendly practices for a greener workplace.